TSMC Certifies Siemens EDA Tools on AWS for N2/N3 Process Node Technology
The semiconductor industry relentlessly pushes technological boundaries. This progress demands ever-evolving design workflows, ensuring optimized performance, efficiency, and scalability. A recent milestone in this evolution is the Taiwan Semiconductor Manufacturing Company (TSMC) certification of Siemens electronic design automation (EDA) tools on the AWS Cloud. This achievement offers significant benefits to semiconductor designers and engineers worldwide.
This certification represents an important endorsement from one of the world’s leading semiconductor foundries. It also demonstrates the shift towards cloud-enabled Siemens EDA workflows, providing enhanced flexibility, performance, and innovation capabilities.
“AWS is pleased to work with Siemens EDA and TSMC on successfully certifying design solutions for TSMC’s advanced N2 and N3 process nodes for customers. This project enables customers to run EDA workloads, share data and collaborate with TSMC in a secure and trusted environment on AWS. The joint effort is testimony to the close collaboration and partnership between the three companies. TSMC advanced node certification is a significant milestone in the EDA on AWS journey.” -Ravi Poddar, Principal Advisor Hi-Tech and Semiconductor Industry, Amazon Web Services.
This report provides a technical overview of the secure, collaborative environment on AWS that TSMC leverages for certifying the N2/N3 process node technology using Siemens EDA software. The project highlights the technical synergies between the three companies. It emphasizes the growing importance of cloud computing in the semiconductor industry.
Secure Cloud Chamber Architecture for TSMC Certification Project

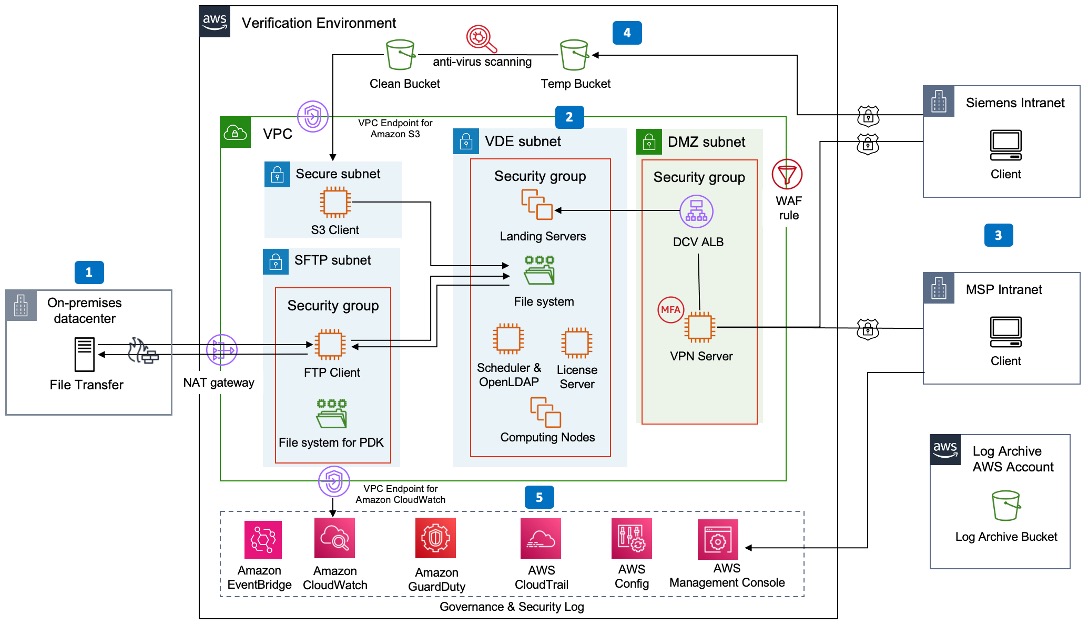
Figure 1: Secure cloud chamber architecture for TSMC certification project on AWS
Figure 1 illustrates the secure cloud architecture deployed for this project, utilizing the AWS industry solution Scale-Out Computing on AWS (SOCA). This custom design accommodates specific requirements from TSMC, including a high-performance compute (HPC) environment that scales to meet project demands and stringent security protocols to protect key assets and intellectual property (IP). The architecture integrates several AWS services and HPC components. These include the scheduler (responsible for job orchestration across diverse queues), the directory service (for user authorization and authentication), a license server (managing Siemens tool licenses), autoscaling compute nodes, and various file systems. These elements are encapsulated within the TSMC Open Innovation Platform (OIP) Virtual Design Environment (VDE).
In addition to the VDE subnet, a secure file transfer subnet grants TSMC personnel access to transfer Process Design Kit (PDK) files and other project-related data from on-premise servers. The Demilitarized Zone (DMZ) subnet provides Siemens product engineers with secure access to the environment through a virtual private network (VPN).
Key data flows and functions within the cloud chamber include:
- Secure File Transfer: TSMC personnel securely transfer the Process Design Kit (PDK), Graphic Design System (GDS), and other project files from on-premise servers to Amazon S3 buckets within AWS.
- VDE Chamber Functionality: Includes the scheduler, directory service (or LDAP), license server, autoscaling compute nodes, and file systems.
- DMZ Subnet Access: Siemens product engineers connect and work within the chamber via VPN. This permits access to PDK and design data, execution of experiments using Siemens EDA tools, and interactive sessions through NICE DCV Display servers.
- Automatic File Scanning: A critical security measure that scans all incoming and outgoing files initially stored in a temporary bucket. This scanning process performs critical cybersecurity checks – including malware detection, and identification of phishing and other vulnerabilities. If the scan confirms security, the files are then moved to a clean bucket for safe use within the chamber.
TSMC Security Requirements for Certification Project
TSMC established a set of key security objectives for this AWS-based certification project, including audit logging/traceability, preventing unauthorized access, and ensuring data security, specifically protecting the PDK. To achieve these security goals, the project team implemented a series of security controls leveraging specific features and services offered by AWS. The critical security services and controls implemented within the chamber include:
- Network Access Control (NACL): Part of Amazon VPC (Virtual Private Cloud), NACL controls and audits traffic at both the IP and protocol levels within a subnet within the VPC. Effectively, NACL acts as a network firewall on AWS. By default, all inbound and outbound traffic is blocked by NACL except traffic explicitly allowed by TSMC to access the chamber.
- Security Group: Complementing the NACL, which functions as a network firewall, a security group acts as a virtual firewall for each compute instance to control inbound and outbound traffic across AWS.
- Virtual Private Cloud (VPC) Flow Logs: VPC flow logs capture detailed information on IP traffic moving to and from network interfaces within the VPC. The flow log data is published which allows analytics via Amazon CloudWatch. Flow logs help monitor the specific traffic reaching compute instances and can determine the direction of the traffic to and from these network interfaces. Flow log data is gathered outside the path of your network traffic, so it doesn’t affect your network throughput or latency.
- Observability and Monitoring: Amazon CloudWatch provides a centralized, unified window for all monitoring functions. These logs, including VPC flow logs, AWS CloudTrail, Amazon GuardDuty, Amazon S3 and all required application logs are all consolidated using Amazon CloudWatch. This allows for the creation of alarms and workflows, which can be triggered in the event of suspicious activities.
- AWS EventBridge: Utilized to diligently track all resources deployed within the security chamber. Any modifications to these resources are automatically captured, with integrated notification capabilities.
- Access Control: Amazon Identity and Access Management (IAM) is a vital tool used to prevent unauthorized access. VPN connections secure user permissions from end devices. Multi-factor authentication provides an extra security layer, preventing unauthorized users from accessing accounts. An Open LDAP directory service manages users, their credentials, and associated privileges. Security groups and web application firewalls (WAF) implement network and application access controls at the IP, port, and protocol levels.
- Data Protection: Access controls and encryption are implemented at the storage level. This includes Amazon S3 and Elastic File Storage (EFS). Besides these standard AWS network and security controls, an automatic scanning mechanism quarantines all incoming and outgoing files. These files are first directed into a temporary bucket. After all security checks are performed, legitimate, secure files are then placed in the secure “clean” bucket for use inside the chamber.
Testing and Results
The primary goal of the project involved the verification of seven of TSMC’s sign-off Siemens EDA production flows. This validation involved comparing their results against TSMC’s recognized “golden values” utilizing selected test cases from TSMC’s 2-nanometer and 3-nanometer accuracy test suites. Test data and golden results were securely uploaded to the cloud test environment, becoming available to technical stakeholders within Siemens.
Methodology
The objective of the accuracy tests was to compare two virtually identical runs: One occurred within TSMC’s secure on-premises chamber and the other conducted in the secure AWS environment. The only difference between the two occurred due to their environments (on-premises vs. cloud). The configuration, version of the tool, and the defined rules, were all identical. The transfer of golden results took place as part of the test package, which included testcase data, setup files, and design rules. The final comparison generated a report, which was ultimately examined by TSMC.
The testing strategies varied. Some involved tests conducted on large numbers of test patterns or within individual small cells. Others involved full-chip designs which were run on host machines that were configured inside the AWS cloud in distributed mode, with communication between one primary host and several remote hosts. In cases with individual test patterns, thousands of individual jobs were submitted to the compute environment.
As the runs progressed, the project team compared the results of each process with TSMC’s golden values. This comparison then automatically produced test reports, which were then made available to TSMC. The team tested accuracy by comparing cloud results with the on-premises run. They also tested parallelism to ensure that parallelism was accurate across multiple cloud hosts. The team undertook diverse testcases covering simulations across AC, DC, transient, RF, and aging analysis – as well as multi-simulations utilizing Monte Carlo methods.
Results
For the Calibre nmDRC, SmartFill, nmLVS, PERC, xACT and mPower tests, the team conducted a single, full-chip run using distributed processing. Within individual test cells, multiple tests were run in parallel across multiple hosts. The results revealed consistent and identical results across both the cloud and on-premises setups.
SolidoTM SPICE and AFS, part of the SolidoTM Simulation Suite, were tested for both accuracy and scalability on various circuits in TSMC N2 process technology. Tested circuits included standard cell, analog and IO circuits, ranging from small to larger design capacity. Single simulation analyses included AC, DC, transient, phase noise, and aging for selective designs, as specified by TSMC. SolidoTM accuracy metrics included bandwidth, phase margin, DC gain, frequency, power, current, phase noise, delay, slew, and leakage—metrics relevant to each design. Multi-simulations for Monte Carlo transient were also done across both single and multiple machines for standard cells, with slews and cell delays used as the accuracy metrics. Those results also showed consistent and identical results on both cloud and on-premises.
“Siemens EDA is pleased this 3-way collaboration showed that AWS cloud meets TSMC’s stringent security requirements for protection of foundry and customer data – giving the fabless semiconductor ecosystem confidence to use the AWS cloud for their most sensitive workloads. This was also an excellent demonstration that the AWS cloud can be leveraged for high accuracy additional surge capacity to run the industry leading Calibre nmPlatform and Solido/AFS workloads.” – Michael White, Senior Director, Calibre Physical Verification.
Conclusion
The collaborative project between TSMC, Siemens EDA, and AWS confirms functional parity when comparing cloud and on-premises environments. Crucially, the cloud environment offers added benefits, including enhanced scalability, flexibility, and cost-effectiveness. The successful certification of Siemens EDA’s signoff flows on AWS provides a high degree of confidence in cloud computing’s capabilities. This opens the way for further adoption in the semiconductor industry. This project underscores the importance of collaboration and innovation in meeting the growing computational needs of the semiconductor sector.
Cloud computing continues to evolve, and it will play a critical role in shaping the future of semiconductor design and manufacturing.
“Our recent collaboration with AWS and Siemens marks a major advancement in semiconductor design workflows in Cloud, enabling next-generation chip design using TSMC’s most advanced process technologies, while providing designers with enhanced efficiency and flexibility. We will continue to work closely with our EDA and Cloud partners to lower the barriers to semiconductor design, helping designers worldwide quickly launch their chip innovations.” – Dan Kochpatcharin, Head of the Ecosystem and Alliance Management Division at TSMC