Microsoft’s Shift to Zero Trust Security Model
At Microsoft, our transition to a Zero Trust security model, which began over seven years ago, has been instrumental in helping us navigate the challenges posed by the increasing prevalence of cloud-based services, mobile computing, Internet of Things (IoT), and bring-your-own-device (BYOD) policies in the workforce.
The Zero Trust Model
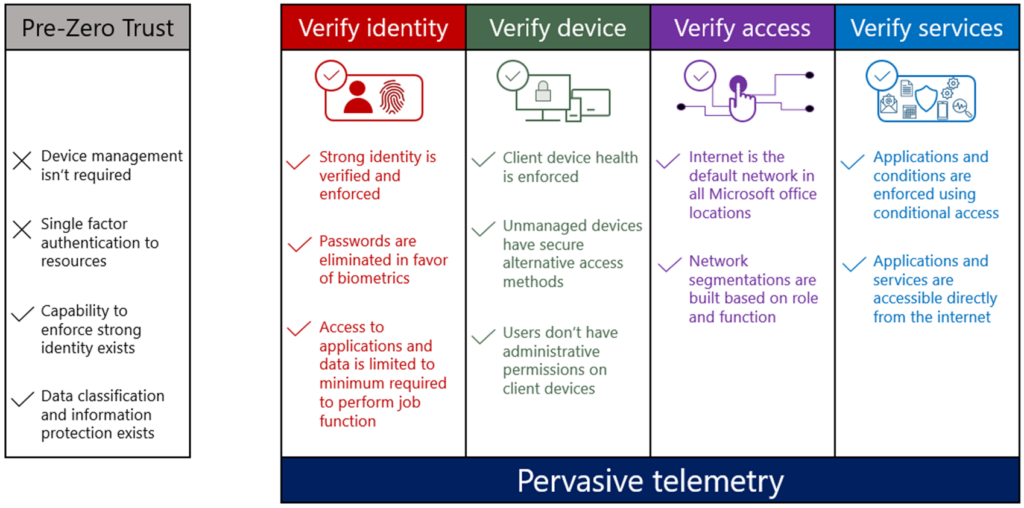
The Zero Trust model is based on the principle of verified trust, where trust is established through verification rather than assumption. This approach eliminates the inherent trust assumed within traditional corporate networks. Zero Trust architecture reduces risk across all environments by establishing strong identity verification, validating device compliance before granting access, and ensuring least privilege access to only explicitly authorized resources.

Key Components of Zero Trust
- Identities are validated and secure: Phishing-resistant authentication (MFA) is used everywhere, eliminating password expirations and eventually passwords. Biometrics ensure strong authentication for user-backed identities.
- Devices are managed and validated as healthy: Device health validation is required, and all device types and operating systems must meet a minimum health state to access Microsoft resources.
- Telemetry is pervasive: Robust and standardized auditing, monitoring, and telemetry capabilities are core requirements across users, devices, applications, services, and access patterns.
- Least privilege access is enforced: Access is limited to only the applications, services, and infrastructure required to perform job functions.
Microsoft’s Zero Trust Journey
We’ve identified four core scenarios to achieve Zero Trust:
- Applications and services validate multifactor authentication and device health.
- Employees can enroll devices into a modern management system.
- Employees and business guests have alternative access methods for unmanaged devices.
- Access to resources is limited to the minimum required.
Our implementation has focused on common corporate services used across our enterprise, starting with core applications like Microsoft 365. We’ve expanded device management to include Windows, Mac, Linux, iOS, and Android devices.

Lessons Learned and Recommendations
Our transition to Zero Trust continues to evolve. We’ve made significant progress in strengthening identity authentication, deploying device management, and reducing dependency on VPNs. To adopt Zero Trust, enterprises should:
- Collect telemetry and evaluate risks.
- Implement modern identity and MFA.
- Focus on conditional access enforcement for critical applications.
- Start with simple device health policies.
- Monitor VPN traffic and migrate users to the internet.
- Prioritize user experience and communicate changes organization-wide.
By following these steps and learning from our journey, organizations can successfully transition to a Zero Trust security model, enhancing their security posture in the modern enterprise landscape.