The Growing Importance of Blockchain Security
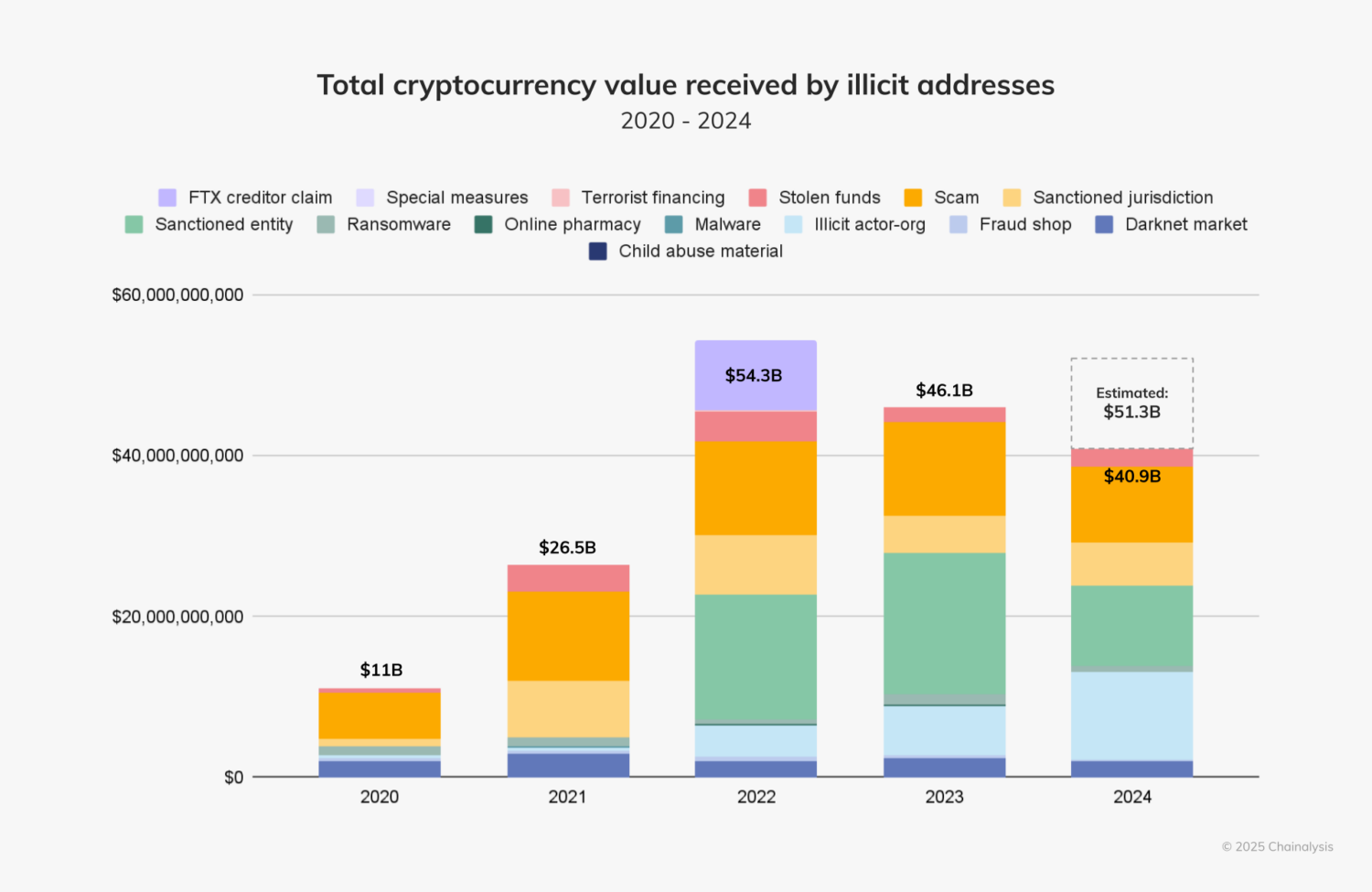
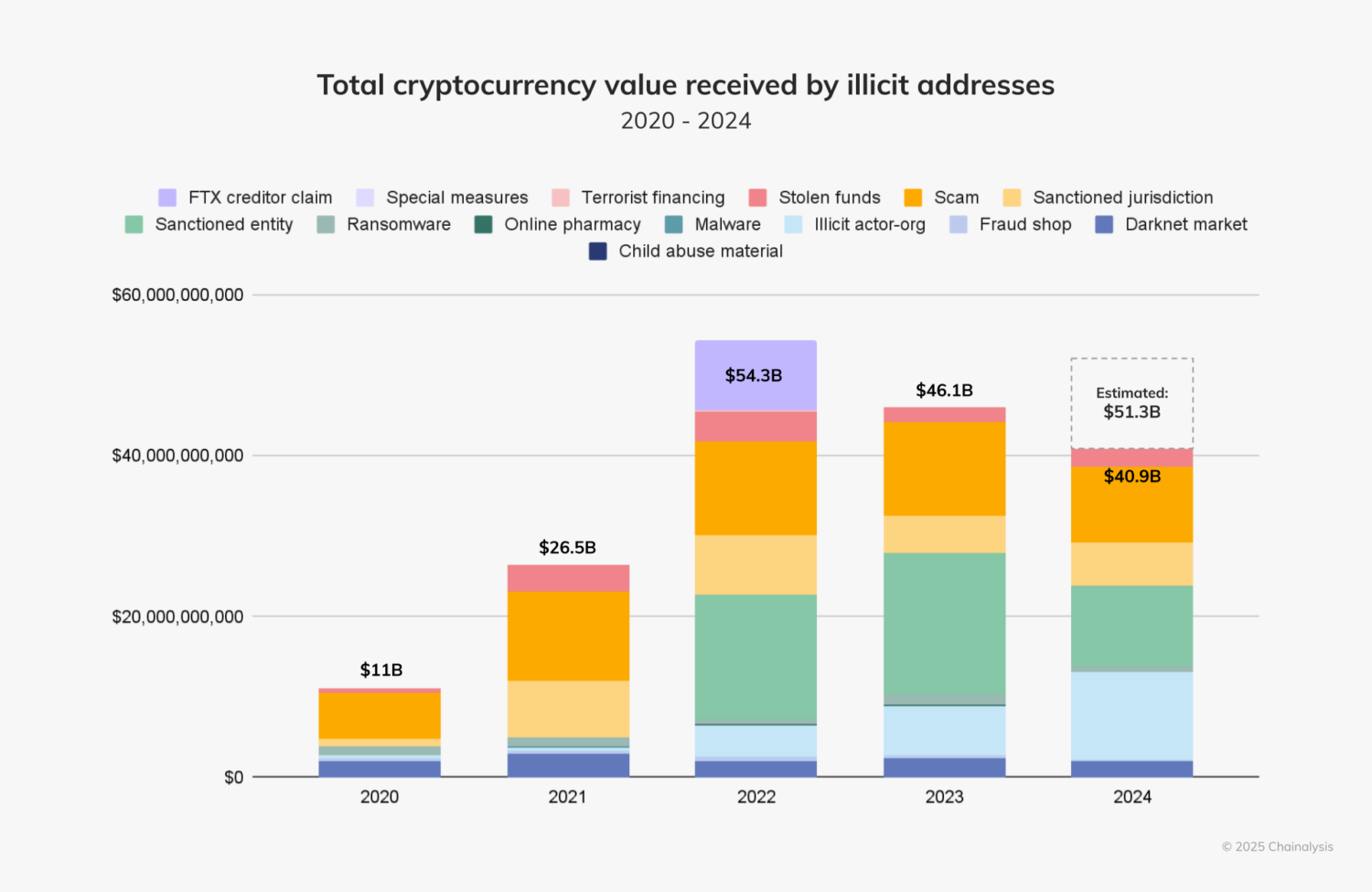
In 2024, illicit cryptocurrency addresses received approximately $40.9 billion, highlighting the urgent need for stronger blockchain security measures. As blockchain adoption accelerates and decentralized infrastructure expands, so does the attack surface. The need for robust blockchain security grows more urgent with every new protocol, smart contract, and wallet user added to the ecosystem.
Understanding Blockchain Security
Blockchain security refers to the combination of cybersecurity principles, tools, and best practices aimed at mitigating risk and preventing unauthorized access while operating on blockchain networks. Both public and private blockchains have their own security models due to their different network structures.
Public Blockchain Security
Public blockchains like Bitcoin and Ethereum are open and permissionless. Their open-source codebase is continually vetted by developers, enhancing security through community scrutiny. However, this openness also allows hackers to search for vulnerabilities.
Private Blockchain Security
Private blockchains are exclusive and permissioned, making them more centralized. Their security is the sole responsibility of the operating entity, with a single point of failure. While generally faster and more efficient, they lack the security-by-numbers approach of public blockchains.
How Blockchains are Secured
Blockchain technology uses a distributed digital ledger system maintained by a network of computers (nodes). Transactions are recorded in blocks and verified through consensus mechanisms like Proof-of-Work or Proof-of-Stake. Cryptography secures transactions, while decentralization and immutability prevent tampering.
Challenges in Securing Blockchains
The rapid pace of innovation in blockchain outstrips the development of security tools, leaving gaps that attackers exploit. The permissionless nature of blockchain allows malicious actors to operate at scale, and cross-chain activity complicates monitoring and security.
Common Types of Blockchain Threats
- Smart Contract Exploits: Attackers exploit bugs or vulnerabilities in self-executing contracts to drain funds or manipulate protocols.
- Oracle Manipulation: Corrupting oracle inputs can trigger faulty contract logic, leading to significant consequences in DeFi.
- Bridge Attacks: Cross-chain bridges are prime targets due to their complex architectures and large funds.
- Phishing Attacks: Scammers trick users into revealing private keys or signing malicious transactions, with nearly $10 billion lost in 2024.
The Role of Blockchain Analytics in Threat Prevention
Blockchain analytics provide visibility into on-chain activity, helping security teams identify red flags early. Key components include address labeling, attribution databases, protocol audits, and cross-chain visibility.
Chainalysis Hexagate: Proactive Blockchain Security
Chainalysis Hexagate offers real-time monitoring and threat detection, empowering protocols to identify and block malicious transactions before damage occurs. It provides preemptive attack prevention, tailored Web3 security, and seamless integration into existing security workflows.
Why Blockchain Security Matters for Adoption
A major blockchain attack can shatter user trust and set back entire ecosystems. Strong, visible security practices are essential for institutional and enterprise adoption. The industry is shifting from reactive cleanup to proactive prevention, requiring continuous investment in security infrastructure and collaboration.